
Introduction to Networking for IT Engineers
 |
Description
Book Introduction
Infrastructure Knowledge You Need to Know in the Cloud/DevOps Era
The days of having separate server rooms and server administrators have passed, and cloud services have become widespread.
With the shift to cloud services, developers are now directly responsible for deploying and testing servers, and network layouts, making infrastructure knowledge essential.
No matter how convenient the interface of a cloud service is, it has become difficult to use the service if you do not understand what a virtual IP is, why you should use DHCP, and how DNS works.
Let's make sure we understand the workings of the lower layers of the network, as well as the upper layers of the network that are familiar to developers.
The days of having separate server rooms and server administrators have passed, and cloud services have become widespread.
With the shift to cloud services, developers are now directly responsible for deploying and testing servers, and network layouts, making infrastructure knowledge essential.
No matter how convenient the interface of a cloud service is, it has become difficult to use the service if you do not understand what a virtual IP is, why you should use DHCP, and how DNS works.
Let's make sure we understand the workings of the lower layers of the network, as well as the upper layers of the network that are familiar to developers.
- You can preview some of the book's contents.
Preview
index
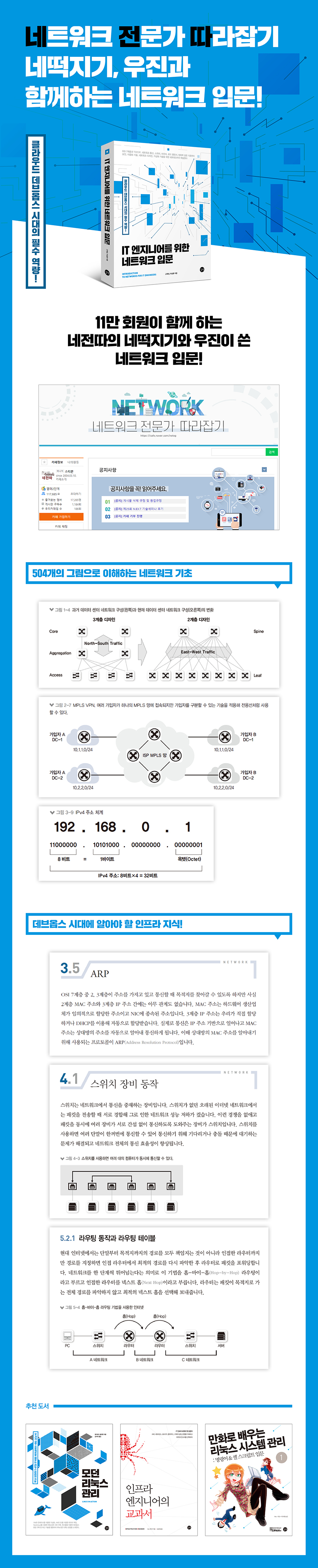
Chapter 1: Getting Started with the Network
__1.1 Looking at the network configuration diagram
__1.2 Protocol
__1.3 OSI 7 Layers and TCP/IP
__1.4 Understanding the OSI 7 Layers
__1.5 Encapsulation and Decapsulation
Chapter 2 Network Connections and Components
__2.1 Network connection classification
__2.2 Network Line
__2.3 Network Components
Chapter 3 Network Communication
__3.1 Unicast, multicast, broadcast, anycast
__3.2 MAC address
__3.3 IP address
__3.4 TCP and UDP
__3.5 ARP
Chapter 4 Switches: Layer 2 Devices
__4.1 Switch Equipment Operation
__4.2 VLAN
__4.3 STP
Chapter 5 Routers/L3 Switches: Layer 3 Devices
__5.1 How the router works and its role
__5.2 Path Designation - Routing/Switching
__5.3 How to set up routing
Chapter 6 Load Balancers/Firewalls: Layer 4 Devices (Session Devices)
__6.1 Characteristics of 4-tier equipment
__6.2 Load Balancer
__6.3 Firewall
__6.4 Things to consider when passing through 4-tier equipment (session management)
Chapter 7 Key Network Technologies that Aid Communication
__7.1 NAT/PAT
__7.2 DNS
__7.3 GSLB
__7.4 DHCP
Chapter 8 Server Network Basics
__8.1 Setting up and verifying the server's network
__8.2 Server's routing table
__8.3 Commands for network verification
Chapter 9 Security
__9.1 Concept and Definition of Security
__9.2 Types of Security Solutions
__9.3 Firewall
__9.4 IPS, IDS
__9.5 DDoS defense equipment
__9.6 VPN
Chapter 10 Server Firewall Settings/Operation
__10.1 Checking and Managing the Firewall of a Linux Server
__10.2 Checking and Managing the Windows Server Firewall
Chapter 11: Duplication Technology
__11.1 Overview of redundancy technology
__11.2 LACP
__11.3 Setting up network redundancy on the server (Windows, Linux)
__11.4 MC-LAG
__11.5 Gateway redundancy
Chapter 12 Load Balancer
__12.1 What is load balancing?
__12.2 Load balancing method
__12.3 Health Check
__12.4 Load Balancing Algorithm
__12.5 Load Balancer Configuration Method
__12.6 Load Balancer Operation Mode
__12.7 Load Balancer Notes
__12.8 Setting up a load balancer using HAProxy
Chapter 13 Network Design
__13.1 Layer 2/Layer 3 Network
__13.2 3-Tier Architecture
__13.3 2-Tier Architecture
__13.4 Data Center Zone/PoD Internal Network/DMZ Network/Internet Network
__13.5 Cabling and Networking
Chapter 14 Virtualization Technology
__14.1 What is equipment virtualization technology?
__14.2 Vendor-specific equipment virtualization technology: Virtualization that creates a single logical device
__14.3 Vendor-specific equipment virtualization technology: Virtualization created with multiple logical devices
Chapter 15 Networking for Virtualized Servers
__15.1 Network settings when configuring a virtual server
__15.2 VMware vSphere
__1.1 Looking at the network configuration diagram
__1.2 Protocol
__1.3 OSI 7 Layers and TCP/IP
__1.4 Understanding the OSI 7 Layers
__1.5 Encapsulation and Decapsulation
Chapter 2 Network Connections and Components
__2.1 Network connection classification
__2.2 Network Line
__2.3 Network Components
Chapter 3 Network Communication
__3.1 Unicast, multicast, broadcast, anycast
__3.2 MAC address
__3.3 IP address
__3.4 TCP and UDP
__3.5 ARP
Chapter 4 Switches: Layer 2 Devices
__4.1 Switch Equipment Operation
__4.2 VLAN
__4.3 STP
Chapter 5 Routers/L3 Switches: Layer 3 Devices
__5.1 How the router works and its role
__5.2 Path Designation - Routing/Switching
__5.3 How to set up routing
Chapter 6 Load Balancers/Firewalls: Layer 4 Devices (Session Devices)
__6.1 Characteristics of 4-tier equipment
__6.2 Load Balancer
__6.3 Firewall
__6.4 Things to consider when passing through 4-tier equipment (session management)
Chapter 7 Key Network Technologies that Aid Communication
__7.1 NAT/PAT
__7.2 DNS
__7.3 GSLB
__7.4 DHCP
Chapter 8 Server Network Basics
__8.1 Setting up and verifying the server's network
__8.2 Server's routing table
__8.3 Commands for network verification
Chapter 9 Security
__9.1 Concept and Definition of Security
__9.2 Types of Security Solutions
__9.3 Firewall
__9.4 IPS, IDS
__9.5 DDoS defense equipment
__9.6 VPN
Chapter 10 Server Firewall Settings/Operation
__10.1 Checking and Managing the Firewall of a Linux Server
__10.2 Checking and Managing the Windows Server Firewall
Chapter 11: Duplication Technology
__11.1 Overview of redundancy technology
__11.2 LACP
__11.3 Setting up network redundancy on the server (Windows, Linux)
__11.4 MC-LAG
__11.5 Gateway redundancy
Chapter 12 Load Balancer
__12.1 What is load balancing?
__12.2 Load balancing method
__12.3 Health Check
__12.4 Load Balancing Algorithm
__12.5 Load Balancer Configuration Method
__12.6 Load Balancer Operation Mode
__12.7 Load Balancer Notes
__12.8 Setting up a load balancer using HAProxy
Chapter 13 Network Design
__13.1 Layer 2/Layer 3 Network
__13.2 3-Tier Architecture
__13.3 2-Tier Architecture
__13.4 Data Center Zone/PoD Internal Network/DMZ Network/Internet Network
__13.5 Cabling and Networking
Chapter 14 Virtualization Technology
__14.1 What is equipment virtualization technology?
__14.2 Vendor-specific equipment virtualization technology: Virtualization that creates a single logical device
__14.3 Vendor-specific equipment virtualization technology: Virtualization created with multiple logical devices
Chapter 15 Networking for Virtualized Servers
__15.1 Network settings when configuring a virtual server
__15.2 VMware vSphere
Detailed image
Publisher's Review
Infrastructure knowledge makes a difference
In the past, knowledge of web development was sufficient, but with the widespread adoption of cloud computing and the rise of serverless architectures that don't even require servers, the need for backend and infrastructure knowledge has become more important.
Developers who understand how a web page's URL request is routed through the infrastructure can make all the difference in figuring out how to resolve issues when they arise.
In this day and age, developers also need to know about infrastructure!
Contents of this book
Network connections and components
TCP/IP and Networking
Router/L3 switch
Load balancer/firewall
NAT/PAT
DNS
GSLB
DHCP
Server Network Basics
Security: FW, IDS, IPS, WAF, NAC, VPN, sandbox
redundancy technology
Network Design
virtualization technology
Network for virtualized servers
Author's Note
There have been rapid changes in the IT market.
The changes that have occurred in the last few years have been far greater than those that have occurred in the past decade or so.
Market changes have expanded the skills required for positions such as developer, server engineer, and network engineer in the traditional IT market.
These changes also began to create new study groups that had not previously existed.
Network engineers are gathering to study Linux, server engineers are forming a virtualization study group to study networks, and developers are gathering to study cloud infrastructure.
These efforts have increasingly blurred the boundaries between the skills required in each field, ultimately making understanding the fundamental elements that make up IT an essential skill for IT engineers.
However, it is still not easy to understand technologies in other fields or to extend one's own skills to other fields.
Moreover, even as understanding of mutual technology increases, we feel more strongly that this boundary is not easily broken down due to differences in perspectives on technology.
It may be because of the engineers' attitude towards technology, but even with the same technology, we often encounter situations where the perspectives on it are different, and the way we understand and explain the technology differs.
Even when it comes to bonding, which is simply using network interfaces together, the way network engineers and server engineers describe and define this technology differs because of the differences in their experiences.
Even if they are engineers who handle the same network, the perspectives of a router engineer who mainly handles Layer 3 and a session equipment engineer who mainly handles Layer 4 and the application layer are very different.
Additionally, even when dealing with the same application layer, network security engineers and load balancer engineers have different perspectives.
While it's impossible to eliminate all these differing perspectives at once, this book has attempted to address the fundamental reasons for the emergence of this technology and the perspectives from which it should be viewed, based on an understanding of the fundamental concepts of networks and related standards.
I wanted to help bridge this gap in perspective, even if only a little.
The goal of this book was to serve as a reference point for understanding network principles in an age where fragmented knowledge is overflowing, with only fragmented information available on the Internet.
As mentioned above, the boundaries of modern IT are breaking down, and we have entered an era where engineers with U-shaped skills are desired, evolving from the traditional T-shaped engineers.
If possible, we should try to understand the historical context and fundamental principles in which the technology was created, and rather than viewing technology solely from a single perspective, we should try to understand the technology from various perspectives.
I hope this book will help developers and server engineers new to networking build a foundation in networking, and help them understand different perspectives within the networking industry.
-Go Jae-seong, Lee Sang-hoon
In the past, knowledge of web development was sufficient, but with the widespread adoption of cloud computing and the rise of serverless architectures that don't even require servers, the need for backend and infrastructure knowledge has become more important.
Developers who understand how a web page's URL request is routed through the infrastructure can make all the difference in figuring out how to resolve issues when they arise.
In this day and age, developers also need to know about infrastructure!
Contents of this book
Network connections and components
TCP/IP and Networking
Router/L3 switch
Load balancer/firewall
NAT/PAT
DNS
GSLB
DHCP
Server Network Basics
Security: FW, IDS, IPS, WAF, NAC, VPN, sandbox
redundancy technology
Network Design
virtualization technology
Network for virtualized servers
Author's Note
There have been rapid changes in the IT market.
The changes that have occurred in the last few years have been far greater than those that have occurred in the past decade or so.
Market changes have expanded the skills required for positions such as developer, server engineer, and network engineer in the traditional IT market.
These changes also began to create new study groups that had not previously existed.
Network engineers are gathering to study Linux, server engineers are forming a virtualization study group to study networks, and developers are gathering to study cloud infrastructure.
These efforts have increasingly blurred the boundaries between the skills required in each field, ultimately making understanding the fundamental elements that make up IT an essential skill for IT engineers.
However, it is still not easy to understand technologies in other fields or to extend one's own skills to other fields.
Moreover, even as understanding of mutual technology increases, we feel more strongly that this boundary is not easily broken down due to differences in perspectives on technology.
It may be because of the engineers' attitude towards technology, but even with the same technology, we often encounter situations where the perspectives on it are different, and the way we understand and explain the technology differs.
Even when it comes to bonding, which is simply using network interfaces together, the way network engineers and server engineers describe and define this technology differs because of the differences in their experiences.
Even if they are engineers who handle the same network, the perspectives of a router engineer who mainly handles Layer 3 and a session equipment engineer who mainly handles Layer 4 and the application layer are very different.
Additionally, even when dealing with the same application layer, network security engineers and load balancer engineers have different perspectives.
While it's impossible to eliminate all these differing perspectives at once, this book has attempted to address the fundamental reasons for the emergence of this technology and the perspectives from which it should be viewed, based on an understanding of the fundamental concepts of networks and related standards.
I wanted to help bridge this gap in perspective, even if only a little.
The goal of this book was to serve as a reference point for understanding network principles in an age where fragmented knowledge is overflowing, with only fragmented information available on the Internet.
As mentioned above, the boundaries of modern IT are breaking down, and we have entered an era where engineers with U-shaped skills are desired, evolving from the traditional T-shaped engineers.
If possible, we should try to understand the historical context and fundamental principles in which the technology was created, and rather than viewing technology solely from a single perspective, we should try to understand the technology from various perspectives.
I hope this book will help developers and server engineers new to networking build a foundation in networking, and help them understand different perspectives within the networking industry.
-Go Jae-seong, Lee Sang-hoon
GOODS SPECIFICS
- Publication date: October 30, 2020
- Page count, weight, size: 596 pages | 1,070g | 183*235*35mm
- ISBN13: 9791165213183
- ISBN10: 1165213184
You may also like
카테고리
korean


korean


![ELLE 엘르 스페셜 에디션 A형 : 12월 [2025]](http://librairie.coreenne.fr/cdn/shop/files/b8e27a3de6c9538896439686c6b0e8fb.jpg?v=1766436872&width=3840)























